SSL Sniffer
Caution
While the name may suggest this software has
packet-sniffingcapabilities, this software only ease thesniffing-processby terminatingTLSin a transparent way.
How to use the software
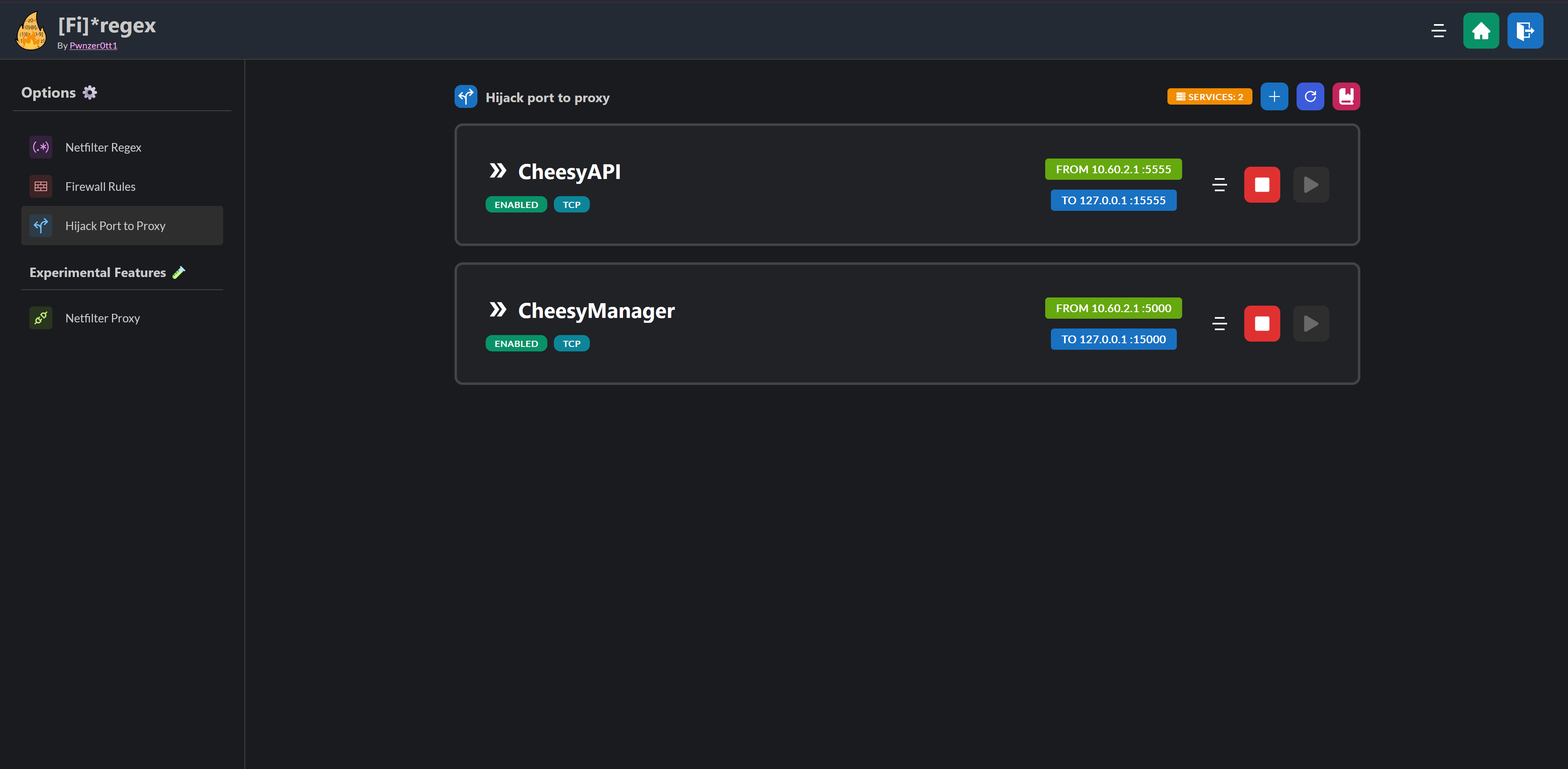
- Have Firegex installed on the
vulnbox(OPTIONAL) - Copy all keys on
ssl-sniffer/private/<service-name>/[key|cert].pem - Copy a template from one of the available templates:
grpc:cp ssl-sniffer/nginx/grpc/conf.example ssl-sniffer/nginx/grpc/<service-name>.confhttp:cp ssl-sniffer/nginx/http/conf.example ssl-sniffer/nginx/http/<service-name>.conf
- Modify the copied template
- Add a rule to hijack the port to the one specified in your conf (OPTIONAL)
- Run
docker compose up -d --build - Check that your service is still reachable
Tip
Remember to capture traffic from the
lointerface, otherwise you won't see any benefit in setting such infrastructure
Full example
Cheesy Cheats-API Template
# CheesyAPI conf
# CheesyAPI TLS endpoint
server {
# Use this to avoid port scanners to know
# what you are using
more_clear_headers Server;
# Here put the TLS termination
# endpoint port
listen 15555 ssl;
http2 on;
# Here put the unencrypted
# endpoint port
location / {
grpc_pass grpc://127.0.0.1:15554;
}
# Put relevant keys here
ssl_certificate /services-keys/CheesyAPI/cert.pem;
ssl_certificate_key /services-keys/CheesyAPI/key.pem;
ssl_protocols TLSv1.1 TLSv1.2 TLSv1.3;
}
# Example Termination endpoint
server {
# Use this to avoid port scanners to know
# what you are using
more_clear_headers Server;
# Here put the unencrypted
# endpoint port
listen 127.0.0.1:15554;
http2 on;
# Here put the original
# service endpoint port
location / {
grpc_pass grpcs://127.0.0.1:5555;
}
}
Description
Languages
Shell
100%